Banzaibet Casino
There are rewards, cash-back, a game store and much more waiting for you! Next we will tell you all the details about Banzai Bet Casino and how to earn as a member of the loyalty program
WHAT TO KNOW WHEN CHOOSING
Banzai bet casino
The website of the bookmaker BanzaiBet is among the greatest locations to go for all sports betting enthusiasts who are looking for excellent odds to bet with and a rapid way to withdraw their money.
The BanzaiBet group holds licenses in multiple jurisdictions, including the Curacao license number 8048/JAZ2022-084. The bookmaker first joined the worldwide market in 2023 and, in the space of just one year, has established themselves as one of the bookies with the most rapid expansion in the business. According to the statistics, there are several millions of visitors per month. The high odds, quick withdrawals, and extensive betting options offered by the BanzaiBet betting company are the primary contributors to the company’s meteoric expansion.
BanzaiBet is driven by a variety of software from a variety of various companies, including as Pragmatic play, Yggdrasil, Amatic, Edorphina, Playing GO, XRoom, GamART, BetSoft, EGT, Playson, Inbet, Vivo Gaming, Evolution Gaming, and others.
- Mobile Applications: iOS, android, PC
- Site languages: Multi-language
- Currencies: BDT, INR, NPR, PKR, LKR, UZS, USD, EUR, RUB, Crypto ETH, BTC, TRON, NEM, etc.
- Types of bets: sports betting, horse racing, live betting, virtual sports, weekly tournaments, Live, results, politics, results, weather, bonuses, cybersports, etc.
- Min deposit: $1
- Maximum winnings: $unlimited
OFFICIAL Banzai bet WEBSITE
OVERVIEW
BanzaiBet is a website that is very simple to navigate and utilize. After going through the quick and easy registration process, you will then be able to start betting right away. The initial deposit requires only one dollar, which is a really low minimum amount. When you are first getting started in the world of betting, it is not necessary for you to risk a significant amount of money.
BanzaiBet is a company that offers gamers a cutting-edge and visually appealing betting product, which has caused the company to experience a surge in customer demand. The BanzaiBet betting company has a strong online presence, which has contributed to the company’s positive reputation.
The desktop version of the website, the mobile version of the website, and apps for both Android and iOS all provide access to the official website. In addition, the applications can be downloaded and installed on your own personal computer. You may get a review of the applications here, as well as read about them.
Banzaibet casino bonus
When you complete the registration procedure and make your initial deposit at BanzaiBet, the welcome bonus is instantly unlocked, however there are some restrictions:
300 USD is the maximum bonus you may receive;
The amount received must be wagered five times;
You must choose three or more options in the accumulator with odds of at least 1.35;
You cannot withdraw the bonus cash until the requirements are satisfied;
The deal cannot be combined with any other offers;
Per player, only one bonus is permitted;
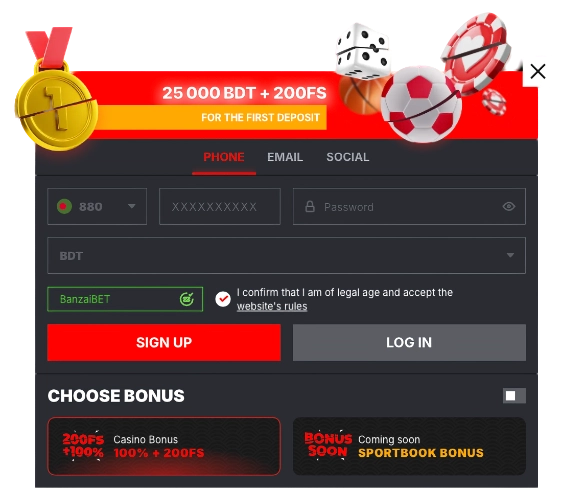
Create an account, then activate your phone number after you’ve finished filling up your profile with all of the pertinent information.
You are required to make an initial payment of at least 5 USD.
The bonus will be added to your account straight away.
Enjoy your gift!
How to claim the Banzai bet bonus
You do not need to be a seasoned gambler in order to understand how to collect the welcome bonus that BanzaiBET provides. Stay with us as we walk you through the steps involved in the process:
When you click on the links that we provide, you will be sent directly to the BanzaiBet homepage.
To create a betting account, you will need to click the red Registration button.
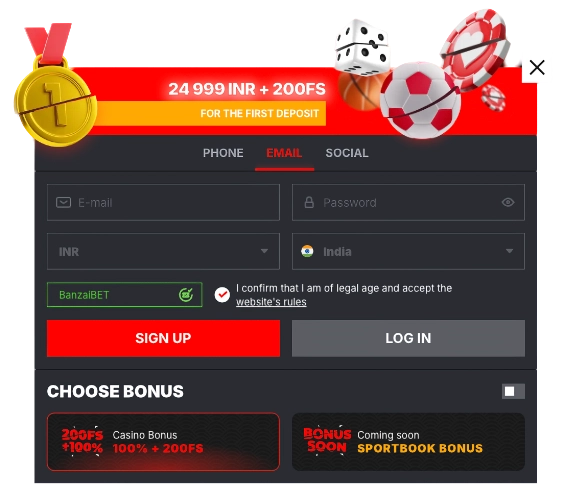
You can sign up for the service using any one of the following four methods: with just one click, over the phone, by email, or via social networks and message services. The one-click technique is the quickest way to do it; all you have to do is select your place of residency and the currency, enter a bonus code if you have one, and then choose the welcome bonus you want to claim. That’s it! When using other ways, you will be required to instantly provide personal information such as your name, email address, physical address, telephone number, and date of birth, among other similar details.
Go to the settings for your account and fill up the player profile there. Make sure that your phone number is registered, as doing so is one of the primary prerequisites for claiming the sign-up bonus packages and using the sports deposit options.
Simply navigate to the “Make a Deposit” section of your profile by clicking on the “Make a Deposit” option, and then choose one of the many available deposit methods.
Please verify the payment.
Your playing account will immediately receive the bonus bet credits when you meet the wagering requirements.
Banzai bet account registration form
Banzai bet account login
Please go through our instructions if you are unsure how to log into your account; if you do so, you will have no trouble doing so. If you do not read through our instructions, you will have no trouble doing so. The only thing that is expected of you is to:
- Visit BanzaiBET. You have the option of doing it via the mobile app or the website.
- To sign in, use the “Sign IN” item from the menu. On the page, you may find this button not far from the “Sign UP” button in the upper-right hand corner.
- Please fill in the blanks with the missing information. Complete the required fields with your email address or user ID, as well as your password, so that you may log in.
- Check to see if you are already logged in. All you have to do is click the “Sign IN” button once again.
- Congratulations, you have been successfully logged into your account! You can also log in using an account from a social network.
- If you forget either your username or password, all you need to do is click the “Forgot your password?” link, and the customer service staff will assist you in regaining access to your account. You can also log in using an account from a social network.
Banzai bet fast games
You are entitled for a bonus of up to three hundred euros and five free spins on the fortunate wheel if you make a deposit of at least one US dollar and play any of the Fast Games that are accessible on the BanzaiBET website.
In order to be eligible for the bonus, you will need to first play through the bonus amount in Fast Games that meet the requirements a total of thirty times within the first twenty-four hours after getting it. The bonus will be rendered invalid and of no use if it is not wagered within the first twenty-four hours of the promotion. When the wagering conditions for the bonus have been met, the bonus funds will become available for deposit to the Account.
Active clients who complete transactions on a daily basis and choose to participate in bonus offers are the only ones who will be eligible to trigger the bonus. This offer is not good for any of the Fast Games that are specifically listed, and it cannot be combined with any other discounts or promotions that are currently available. There is a chance that the availability of the offer might be different on mobile devices compared to desktop computers, and that this could change at any moment.
Aviator BanzaiBET (Crash Games)
You have the option of boosting the amount you wager in the online game Aviator all the way up to a maximum of x1200 if you want to improve your chances of coming out on top. This is done in consideration of the likelihood of the outcome. This suggests that by placing a bet of only one dollar, you have the ability to gain one thousand two hundred dollars almost instantly.
Aviator is the latest and greatest in terms of the satisfaction that can be gained from playing games. You have a good chance of winning a substantial sum of money very quickly. The only way that can currently offer a genuine assurance of fairness in the gaming business is the provably fair technology, which forms the basis of Aviator Spribe.
The Aviator algorithm is an easy one to understand. Every round has betting. The rate of multiplication is being accelerated by AI. Bets that have not yet been cashed out are voided when the coefficient suddenly stops increasing.
Aviator Spins game results from the online casino are guaranteed to be fair and unbiased according to the technology known as Provably Fair. The coefficient for the round’s outcome is not generated by online casinos when it is time for the plane to take off. Participants in the round are the ones who come up with it. Everything is in plain view. Anyone may verify that the game is being played fairly.
Bet and Cashout are both Features
Choose your bet, then press the Place Bet button.
Increase or decrease your bet based on the odds. Before each new round, a trustworthy random number generator delivers a coefficient that determines the speed at which the airplane takes off. Within the game industry, the only system that can be demonstrated to be fair is the one that Aviator Spribe uses.
To cash out your winnings, click the Cashout button. Multiply your bet by the probability of winning for that particular gaming session.
Autostart, Autoplay, and AutoCashout
Clicking the checkbox located next to the Autobet line activates autoplay when the Auto option is selected in the betting panel. Following activation, the wager will be predetermined; nevertheless, you will need to click Cashout before each round in order to remove any winnings. There is also the option of using AutoCashout.
One of the options available in the betting panel is referred to as AutoCashout. Once the feature is activated, your stake will be automatically removed whenever it meets the odds you specified.
Dice
The game of dice is one of the earliest and most popular forms of gambling. For decades, it has provided players from privileged backgrounds all over the world with the opportunity to grow their riches. Studies of history have shown that humans have been playing games with rules and mechanics theoretically comparable to “Dice” as far back as Ancient Egypt and Ancient Rome.
You do not have to have everyone gathered around the tree and shake a few dice with markings on them like you used to have to do in the old days. You can put your luck and intuition to the test with only a few clicks by heading to BanzaiBET Games.
In addition to the table and the dice, there are a number of other elements displayed on the screen of the game. These items include the following:
A betting panel that consists of buttons for the purpose of making selections more quickly. You have the option of manually defining the exact amount by first clicking on the input field and then making the necessary adjustments with the keyboard. If you wish to dial a sum that is a multiple of either 50 or 100 or 1000, you can do so by clicking on the buttons that are provided. To get the number 4550, for example, you need to click the button a total of four times in the range 1000–500–50. If you want to clear the input field, all you have to do is click on the tiny button shaped like a cross.
Auto Play. If you do not want to be required to continually altering the stake or pushing the “Play” button at every available opportunity, you should set this toggle switch to the active position.
Make a connection to the guidelines. In the top-left corner of the screen, there is a box labeled “HOW TO PLAY? Simply clicking on it will provide you information about the guidelines for the game as well as the sequence in which it should be played.
Banzai bet slots
BanzaiBET offers a huge selection of slot games, including everything from the most current releases to the most popular classics. Additionally, the BanzaiBET website offers demonstration versions.
Poker
Everyone knows about the game, but not everyone is familiar with its rules. Both the table and the players’ hands will fill with cards as the game progresses. While attempting combos, players bet. At the conclusion of the game, the player who can pull the highest combination off the table wins.
Blackjack
Since blackjack is a straightforward game, many novice gamblers begin there. The object of the game is to get as close to 21 points with your hand combination. While the game is being played, the client may finish their cards, but if their hand totals to more than 21, they forfeit.
European Roulette
The player must place their wagers in the roulette wheel’s sectors, which are represented by the colors and numbers. After the bets are put, the wheel begins to spin and the ball is dropped onto it. The wheel then keeps turning for a while before stopping. If the ball lands in the selected sector when the wheel comes to a stop, the wagerer is considered to have won the round.
Sic Bo
Sic Bo is a simple dice game that depends on good fortune. Simply put your chips in the bet box on the table to start playing. If the result of the roll matches your wager after the dice have been shaken, you win. Sic Bo provides a variety of bets, each with a different reward probability.
Dynamic Tiger
When playing Dynamic Tiger on BanzaiBET, you only need to choose your bet size and whether to wager on the dragon.
Gates of Olimpus
Many of the gameplay elements and features found in other well-liked games from the software provider, such Sweet Bonanza, are also included in this incredibly volatile slot machine. The most current offering from renowned software provider Pragmatic Play, Gates of Olympus, was only recently made available.
Excitement is increased with special multiplier icons with arbitrary values between x2 and x500. The primary and bonus games on Gates of Olympus contribute to a non-resetting multiplier during FS. It greatly benefits gamblers. In the base game, these symbols are in charge of significant wins.
Sweet Bonanza
BanzaiBET Sweet Bonanza, a 6-reel, win-all-ways slot from Pragmatic Play, has a lot of sweets and fruit. The Tumble feature lets you win frequently by starting a series of events that swap out and add winning symbols. Although it has been there for a while, it is growing in popularity since it increases gameplay and allows players to engage with the slot like they would with cross-platform video games.
Buffalo Slots
The most well-known 5-reel, 4-symbol per reel slot machine is the uffalo. It has wilds, scatters, and free spins. According to our rules, you can use the buffalo, tiger, eagle, and wolf symbols to win huge in-game jackpots with significant virtual rewards. For real money betting, review our betting policies.
Another no-charge online slot machine, Golden Goddess has a $2,513,441.20 jackpot and a 94.75% RTP. Download the Buffalo casino game for free to learn how to win big. Play with strategy for free online without downloading on iPhone, Android, and iPad. Medium volatility, 25 paylines, and a $12,000 jackpot.
Fruit Party
Fruit Party was made by Pragmatic Play. When it was released on May 21, 2020, gamblers adored its exhilarating engine and superb artwork. Our free demo mode and this review provide you a complete understanding of its key attributes.
Fruit Party takes place on a lush meadow decorated with vibrant and delectable fruit symbols. The Fruit Party slot machine uses the Cluster Pays feature and has a large 7-by-7 playing area. Win if five identical symbols touch each other either horizontally or vertically.
Fruit Party’s winning clusters vanish and are replaced by fresh ones. This function enables multiple spin wins. Join the fruit party on any device by wagering between $0.20 and $100 per spin. Fruit Party offers a maximum payout of 5000x, 96.50% RTP, and moderate volatility.
Book of Rampage
Making Book of Rampage slots is Spinomenal. Try it or one of the widely played casino games. You can begin the game by selecting “Spin.” Slot machines are explained in our online slots tutorial.
Fans of both conventional and unusual games will enjoy Book Of Rampage. Even without the bonus, the game is more entertaining because to wilds, scatters, and other unique symbols or features.
Game analytics can aid in making decisions. Book Of Rampage has a maximum win of x5000, an average volatility, and a 95.9% return. The game is intriguing since the arithmetic model is balanced and there are large swings. It has excellent gaming.
Sun of Egypt
With 10000 credits and 25 paylines, Sun of Egypt 3 is a distinctive and flexible slot from Booongo that mimics the most well-known slot machine subject among the literature. The slot machine offers the most enjoyable experience imaginable. Stunning environment can be seen in Sun of Egypt 3.
This slot’s advantage is 4.39%, while the RTP is 95.61%. The slot machine features wild symbols, scatter symbols, free spins, hold and spin, mystery symbols, re-spins, bonus games, and bonus signs. You can use any mobile device to play the game.
Banzai bet online casino
Both the BanzaiBET website and the BanzaiBET mobile app offer players access to more than 8,000 different casino games, including a selection of live dealer games. The total number of games offered exceeds seven thousand.
All of the games that are available are powered by software that was developed by reputable companies. Some of these companies include Evolution Gaming, Pragmatic Play, Yggdrasil, Booongo, Endorphina, Spribe, Playson, Platipus, and NetEnt. There are five distinct sections within the casino, and additional information regarding each section may be found further down on this page.
The BanzaiBET casino APPS is the bookmaker’s official mobile casino gambling application. Downloading the BanzaiBET apk file onto an Android or iOS mobile device enables users to take part in online casino games offered by BanzaiBET as well as wager on sports events using those devices.
The BanzaiBET online casino app streamlines and accelerates the betting process for all of favorite sporting events. In this evaluation of the BanzaiBET app, we will examine the application in its entirety, focusing on each and every one of its features as we do so.
Lighting roulette
Lightning Roulette is a form of online roulette that can be played with real money and features a live dealer as well as a chat area for both the players and the host of the game. You have a one dollar chance to win five hundred dollars.
In Lightning Roulette, the object is to determine the number that the roulette ball will hit before placing a bet on that number. On the roulette wheel are the numbers 1 through 36, as well as 0. Both the first (18-36) and the second (19-36) portions of the field’s numbers are denoted by red and black columns, respectively. There are three dozen: 1v12, 13v24, 25v36. Also odd/even. “Zero” is a second example.
Bets can be placed on individual numbers as well as groupings of numbers, such as dozens, columns, even/odd, black/red, and so on in Lightning Roulette, which is based on French roulette. Inside bets and outside bets are determined by whether the cell in question is located within the main field or closer to the field’s perimeter. Bets on Lightning Roulette in online casinos operate on the basis of this principle.
Following the collection of wagers, a “lightning” will select random numbers between 1 and 5 with odds ranging from x50 to x500. Bonuses assure big gains!
Lighting Dice
Lightning Dice is a one-of-a-kind live casino game that was developed by Evolution Gaming. Published on the 1st of June, 2019. Because the Lightning function from Lightning Roulette is also present in Lightning Dice, you will find that you enjoy using it. This easy yet entertaining live casino game is available around the clock.
Today, we will discuss everything there is to know about this amazing game. Learn the game’s rules and different strategies to improve your performance. This is our fourth post covering the Evolution Gaming game show. Other than that, we also have articles like “Gonzov’s Treasure Hunt,” “Crazy Time,” and “Deal or No Deal Live.”
Crazy Time
The popular wheel of fortune for money was the inspiration for the fun game show known as Crazy Time, which was a spin-off of the original game. The host of the game is the one responsible for rotating the massive wheel that sits vertically in the middle of the playing area and is divided into 54 distinct sections. In addition to this, the wheel is spun repeatedly to select a random multiplier for each time it is used.
The goal of the game is to properly anticipate which section of the wheel will be in play when the wheel finally comes to a stop. In addition, there are bonus games in Crazy Time, and you can win multipliers by participating in those games. You only have to place your bets on the various betting areas that are offered in the bonus game, and then watch as the multipliers that you receive add up to enhance your overall balance.
Fun Tun
Fan Tan, the 2021 Version of Evolution Live live dealer table. The first Fan Tan game from Evolution is scheduled to release in 2021. A Chinese bead game known as Fan Tan has been brought back to life. Estimate the number of beads that are still in the collection after it has been divided into four halves. The most recent iteration of Evolution’s live dealer games comes with a return to player percentage (RTP) of 98.75%, high volatility, and a wealth of incentives.
Asian-themed live dealer gambling is what you’ll find at Fan Tan Live. The game is simple to play, but there are a lot of different betting options, which could be overwhelming for beginner players.
Beads or beans may be used in the game. A dome serves as storage for the beads at the dealer’s shop. When the game starts, the dealer will use a metal cup to pick beads out of the extensive collection in a manner that is completely random. The dealer will then use a stick to separate the beads that are within the metal cup into lines of four beads each. Bets are placed on the beads that are still on the final line.
In general, Fan Tan operates according to the aforementioned standards. Standard and extra bets are both available during the Evolution Fan Tan live event. In the basic game display, you have the option of placing eight standard bets. The upgraded display includes twenty additional possible betting combinations. You are able to change Views, but you cannot do so during a round in which wagers are being made.
The player must place a bet on one of the available wagering options. Bets vary from 0.20 to 5,000. The return to player percentage ranges from 96.25 to 98.75%, depending on the bets placed.
Monopoly
MONOPOLY Live is a variation of the famous board game that can be played live online. The primary objective of the game is for players to correctly predict where the giant, vertically mounted Monopoly wheel will come to a stop as the digital version of MR. MONOPOLY patiently waits in the background.
A “CHANCE” segment, a “2 ROLLS” segment, and a “4 ROLLS” segment are also included on the wheel. These “CHANCE,” “2 ROLLS,” and “4 ROLLS” segments award instant cash prizes and multipliers. With these last components, you can begin playing an engaging augmented reality 3D bonus game based on MR. MONOPOLY.
Players stake their wagers on the number that the roulette wheel will come to rest on, which might be 1, 2, 5, 10, “2 ROLLS,” or 4. If players bet on the correct number, they earn various payouts, such as 1 to 1, 2 to 1, 5 to 1, etc.
When the wheel lands on “CHANCE,” Mr. Monopoly hands each player one of the game’s Chance cards. The card displays a cash reward or multiplier bonus that is chosen at random.
If the Chance card shows a multiplier bonus, the player’s bets will be maintained. The presenter gives the wheel another spin, which results in the winnings being multiplied by the multiplier. In the event that the player acquires an additional multiplier, it will multiply!
In order for players to participate in the Bonus game, they must first wager “2 ROLLS” or “4”. When the wheel comes to a stop on “2 ROLLS” or “4”, the bonus game will begin. In the Bonus game, players who have met the requirements can interact with MR. MONOPOLY in his augmented reality 3D Monopoly realm and win prizes, multipliers, and other perks.
Rolling dice will determine the path. In the money wheel game, players who place bets on “2 ROLLS” and “4” are eligible to participate in the Bonus game. The Bonus game can be viewed and enjoyed by players even if no wagers are placed, but they will not be eligible for any rewards.
Banzaibet mobile application
The mobile application for BanzaiBET is incredibly easy to use, has a high level of user friendliness, and responds quickly to user input. Because the tabs that link to the various sections of the sportsbook and casino are conveniently situated in places that are simple to view, all it takes to switch from live betting to casino games is one tap on the screen. This is because the tabs link to the various sections of the sportsbook and casino.
It is not necessary for you to have the most recent version of either the iPhone operating system or the Android operating system in order to download the application because it is compatible with the majority of mobile devices.
BanzaiBET APK
Users of Android devices will be required to download the.apk file directly from Banzai.bet because the Google Play Store does not presently provide gambling with real money. Those who use iOS are subject to the same limitations.
Downloading the BanzaiBET App
Before you can download and install the BanzaiBET app on your mobile device, you will first need to ensure that it has the capability to operate software that was got from a source that is not reliable.
The procedure that must be used in order to develop applications for Android is as follows:
To get the installation process started, go to the “Download” section of the menu.
You can enable the installation of programs from untrusted sources on your device by heading to the Settings menu and making the necessary adjustments there. This will allow you to update the settings on your device.
Locate the.apk file that you downloaded, choose it from the drop-down menu that appears when you click the Install button, and then wait for the installation to finish before moving on.
However, things are a little bit different for individuals who make use of iOS. Please follow these instructions in order to get started with the BanzaiBET app on one of these devices:
You may view your Apple ID by going into the settings of your iPhone or iPad, tapping the menu that displays, and then selecting iTunes and the App Store. After that, you will be prompted to enter your password in order to view your Apple ID.
After you have read and agreed to the user agreement, the following data should be typed into the address fields: street x, city x, postcode x, and phone x all lead to the same place.
Find BanzaiBET by going to the app store, doing a search for it there, and then following the instructions that come up on the screen.
How to deposit and withdraw money in Banzaibet

After verifying your account, you can deposit using one of BanzaiBET‘s several payment methods and start playing.
Successful deposits require the following steps:
- Log into your account.
- To deposit, click “Make a Deposit.”
- Select one of the deposit options:Bkash, Nagad, Rocket, PhonePe, UPI, Gpay, PayTM, CellPay, Easypaisa, JazzCash, UZcard, Visa, MasterCard and crypto.
- Simply input the deposit amount.
- Submit bonus codes here.
- Follow screen prompts to complete the purchase.
- Your gaming account should get funds quickly.
BanzaiBET withdrawal conditions:
Although BanzaiBET withdrawal may be quite quick, there are a number of restrictions. The following requirements must be met in order to conduct a BanzaiBET withdrawal:
If the deposit or withdrawal amount does not match the bet the bettor placed, your withdrawal request will be denied.
Your withdrawal request would be turned down if your betting account had been used fraudulently.
Your withdrawal request will be denied if the payment information you provided for your deposit and what you want to use for withdrawal conflicts.
You shouldn’t conduct a BanzaiBET deposit and withdrawal using the account of another user if you want to use the cash out BanzaiBET effectively. The BanzaiBET payment system would regard that as dishonest.
Your withdrawal request will be rejected if you violate BanzaiBET‘s company policies and do not adhere to the terms and conditions (for example, making a withdrawal without gambling on any games or not meeting the wagering requirement to receive a bonus).
While service fees could apply to bank payment choices, BanzaiBET deposits and withdrawals made using Bitcoin and other cryptocurrencies that are part of the Bitcoin payment system are free of charge.
You must keep the following in mind in order to comply with the BanzaiBET withdrawal requirements; else, your withdrawal request will be rejected.
FAQ Banzaibet

Can Bangladeshi or Indian sign up in BanzaiBET?
The official website suggests that players can gamble on the site without worrying about its legality. The bookmaker has a prestigious gambling license.
What does it take to register at BanzaiBET?
BanzaiBET registration is completely free. Also, it is possible to do so with a single click, after which you will be granted an account name and password that will be forwarded to your specified e-mail address.
Is live streaming available on BanzaiBET website?
Yes, most popular event have live video broadcasts at official BanzaiBET website.
How old do I have to be to bet and gamble with bookmaker BanzaiBET?
You have to be at least 18 years old, as stated by the site’s policies.
What is the minimum available bet?
The minimum single selection bet is €0.20/$0.30.
What is the maximum available bet?
The maximum allowed bet is determined on a case-by-case basis, with the maximum payoff limited at €800,000.
What are the withdrawal limits?
The minimum withdrawal amount is €1.50. The payment system operator determines the maximum available withdrawal, which is normally set at €25,000.
How long does withdrawal usually take?
The process normally takes no more than an hour for players. The processing of withdrawals from an electronic wallet is quicker.
I can’t install the BanzaiBET App, why?
To use the BanzaiBET app, you must modify your Android phone’s “Unknown sources” setting. The BanzaiBET App for users is accessible on iOS and Android devices. For information on how to download and install the app, see the website.
Can I create multiple accounts and bet from them at the same time?
You can set up accounts for your family members, but not more than one for you. If BanzaiBET discovers that you are using multiple accounts, the money will be transferred to you and your blocked accounts.
How do I recover my password if I have forgotten it?
If you are unable to log in to your Personal Area, click on “Restore password”. After that in the special window enter the phone number and e-mail indicated during registration, date of birth and log in.
Is BanzaiBET casino legit?
BanzaiBET, it’s the truth. They are legitimate because they hold a license from the Curacao Gaming Authority. They also enjoy a sterling reputation as a casino that treats its patrons with the utmost respect in the gambling sector.
What is the wagering requirement in BanzaiBET casino?
It’s 30x for both the bonus cash and the free spins.
How do I delete my BanzaiBET account?
A self-exclusion program or a “take a break” tool that lets users lock their accounts for 1, 7, or 30 days are two ways to do this.
Banzaibet Game Attribution
The wager is the number of bets required for the player to withdraw the bonus. The coefficient of the wager is a coefficient calculated by the formula: amount of bets / bonus denomination.
Game Attribution is the percentage of turnover (in money), which is taken into account for the fulfillment of the conditions of the wager on the bonus funds rollover or fulfillment of the terms of the promotion.
Example:
You have received a bonus with a denomination of 200 EUR and a wager coefficient of 30.
To work out this bonus, you need to bet a total of 6000 EUR (200 * 30).
If you choose a game with a 100% Contribution, the calculation of the necessary turnover will be calculated as (200*30)/100%=6000 EUR, if you bet with a 10% Contribution, the calculation will be as follows: (200*30)/10%=60 000 EUR
The banzaibet website has applied the following game attribution:
Casino section
– Slots (except Video Poker) – 100%
– Poker, Video Poker, Roulette, Baccarat, Blackjack, Table Games, Lotteries, Scratch Cards, Bingo, Keno – 0%.
Live Casino section
All categories – 0%
Live-games / TV-games section
-All categories – 10%
Crash (Aviator, Jetx and others) – 1%
Banzaibet support team
If you run into any problems when using the BanzaiBET website, whether it is with your deposits or withdrawals, don’t hesitate to get in touch with customer support. The customer service representatives will do their best to assist you and solve the problems you’re having.
Contact information:
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
Department of Security: [email protected]
Marketing and public relations: [email protected]
Inquiries about partnerships: [email protected]
What do I do if my account is locked?
The casino security service has the right to block game accounts if suspicious activity has been detected on them or if these Gambling Rules have been violated.
To restore access to your gaming account, please contact support or follow the instructions:
Write an e-mail to [email protected]. Specify in it your gaming account number, number of the linked phone or e-mail address, as well as attach the following documents:
1) a photo (selfies) of you holding your passport with data page and personal photo next to your face
2) a photo of the data and photo pages of your passport or other available documents: driver’s license, birth certificate, ID Card.
Photos should be of high quality, data should be visible and easy to read.
The issue of unlocking your account will be resolved as soon as possible, and the status decision will be sent to your e-mail or SMS.

Evolut Interactive N.V. (Curacao). The website operates under the gaming license Curacao No 8048/JAZ2022-084. Payment support operator: Nevadin LTD. Registration number: HE 433770. Legal address: Agias Zonis & Thessalonikis, NICOLAOU PENTADROMOS CENTER, Floor 10, Flat/Office 1001A, BLOCK B, 3026, Limassol, Cyprus (BanzaiBET ru, BanzaiBet)